Global overview
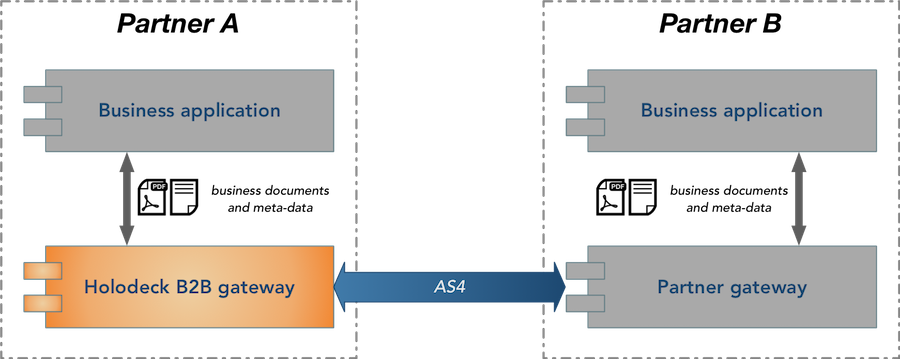
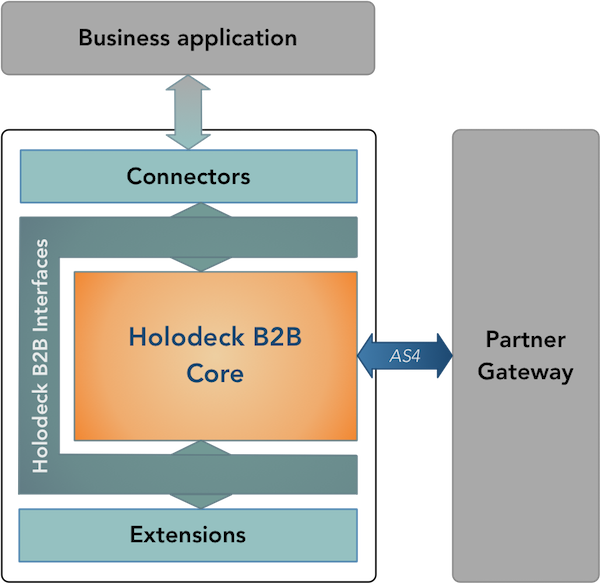
Holodeck B2B is a standalone application that provides the messaging capability to your solution. The Holodeck B2B gateway takes care of all complexity related to messaging protocol used for the message exchange with your trading partner, the business application only needs to provide the business documents and some meta-data telling Holodeck B2B who to send the data to.
The default distribution available for download provides the AS4 messaging capability and has an easy to use file based integration method with the business application.
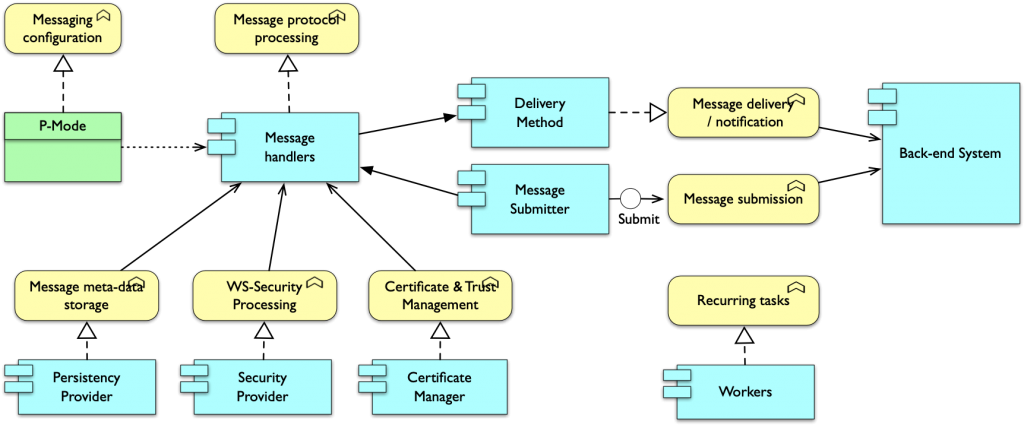
Using Holodeck B2B’s extension mechanism additional functionality, like for example AS2 messaging capability or REST back-end integration can be easily plugged into the gateway. This allows you to create a gateway tailored to the specific requirements of your environment.